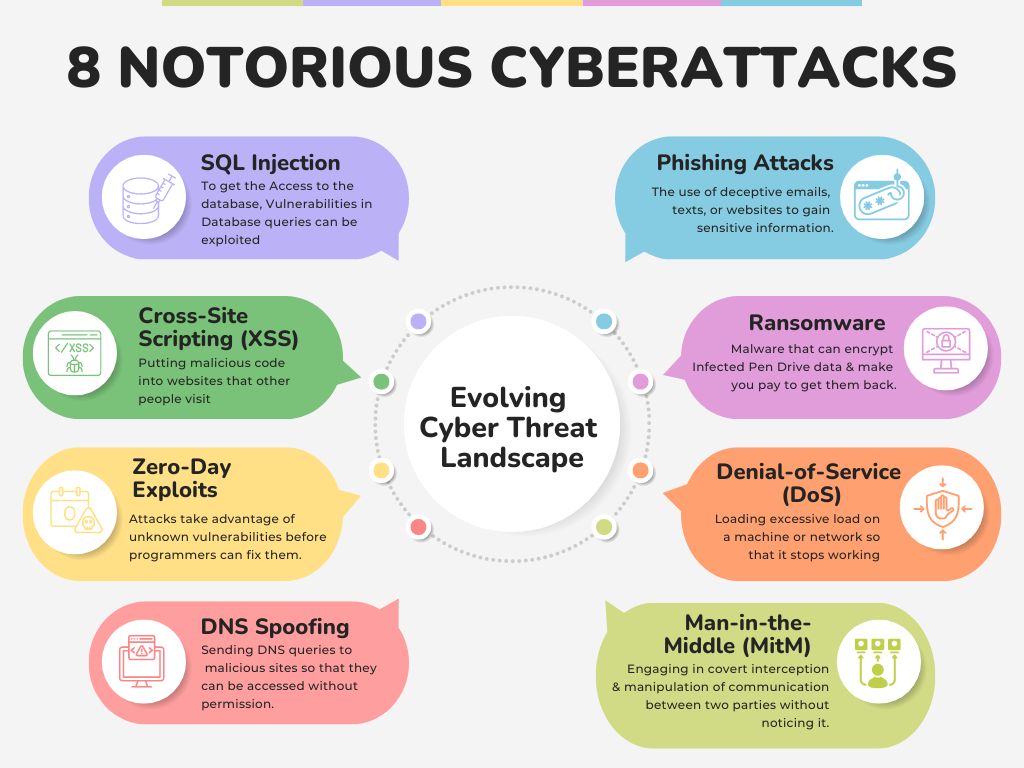
8 Notorious Cyberattacks: A Stark Reminder of the Evolving Cyber Threat Landscape
In the rapidly evolving digital landscape, cybersecurity has become a critical concern for businesses and individuals alike. Cyberattacks are becoming more sophisticated and frequent, posing significant threats to sensitive data, financial assets, and organizational reputation. Understanding the major types of cyberattacks is the first step in safeguarding your digital infrastructure. In this article, we’ll explore eight major types of cyberattacks that every organization should be aware of.
1. Phishing Attacks
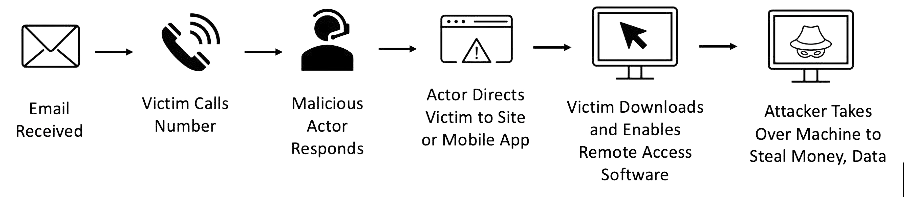
Phishing is one of the most common and effective types of cyberattacks. It involves the use of fraudulent emails, messages, or websites that appear to be from legitimate sources to trick individuals into divulging sensitive information such as usernames, passwords, or financial details.
How It Works:
Attackers often send emails or messages that seem to come from trusted sources, like banks or well-known companies. These messages usually contain a link to a fake website that closely resembles the real one. When the victim enters their credentials, the attackers capture this information and use it to gain unauthorized access to accounts or systems.
Impact:
Phishing can lead to significant financial losses, identity theft, and unauthorized access to sensitive systems. It’s a gateway to more severe attacks like data breaches and financial fraud.
Prevention:
Employee training and awareness are crucial in preventing phishing attacks. Implementing email filtering, multi-factor authentication, and regularly updating security protocols can also reduce the risk.
2. Ransomware
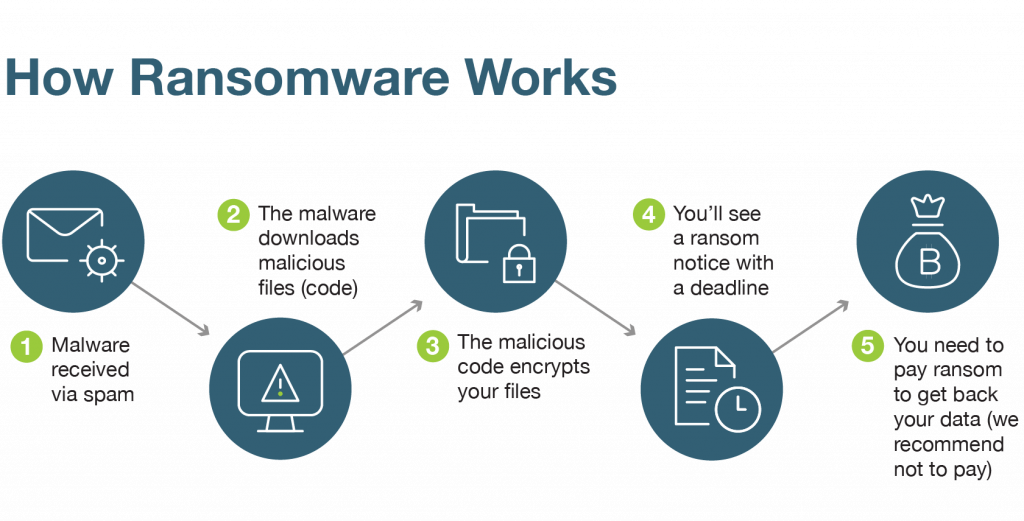
Ransomware is a type of malware that encrypts the victim’s data, making it inaccessible. The attackers then demand a ransom, usually in cryptocurrency, in exchange for the decryption key.
How It Works:
Ransomware often spreads through phishing emails, malicious downloads, or vulnerabilities in software. Once the malware is activated, it encrypts files and displays a ransom note, demanding payment for the decryption key.
Impact:
Ransomware can cripple businesses by making critical data and systems unavailable. Even if the ransom is paid, there’s no guarantee that the data will be restored, and organizations can suffer significant financial and reputational damage.
Prevention:
Regular data backups, up-to-date antivirus software, and strong email security practices are essential in preventing ransomware attacks. It’s also vital to have an incident response plan in place.
3. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
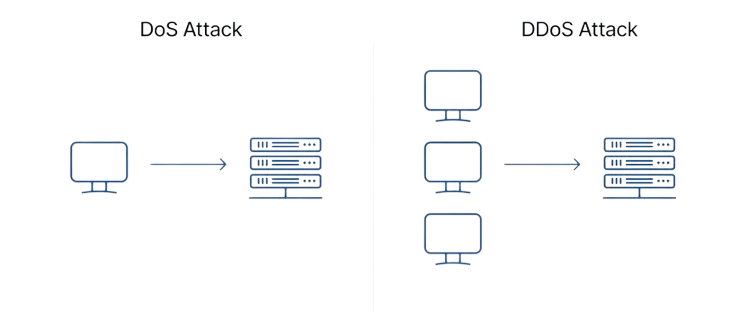
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks are designed to overwhelm a network, service, or website with a flood of traffic, rendering it unavailable to users.
How It Works:
In a DoS attack, the attacker uses a single computer to flood a target with requests. In a DDoS attack, multiple compromised systems, often part of a botnet, are used to generate overwhelming traffic. This disrupts normal traffic and can take the target offline.
Impact:
These attacks can lead to significant downtime, lost revenue, and damage to a company’s reputation. In some cases, they may also be used as a smokescreen for more intrusive cyberattacks.
Prevention:
Implementing network security measures such as firewalls, intrusion detection systems, and traffic analysis can help mitigate the risk of DoS and DDoS attacks. Using a Content Delivery Network (CDN) and having a robust incident response plan are also effective.
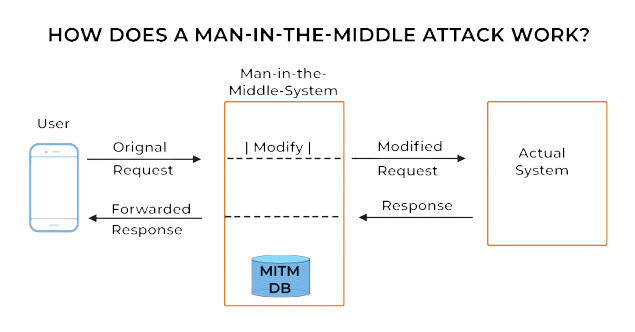
4. Man-in-the-Middle (MitM) Attacks
A Man-in-the-Middle (MitM) attack occurs when an attacker intercepts and alters the communication between two parties without their knowledge. This type of attack is often used to steal sensitive information like login credentials or financial data.
How It Works:
MitM attacks can occur through various means, including unsecured Wi-Fi networks, compromised devices, or fake websites. The attacker secretly relays and potentially alters the communication between the two parties, making it appear as though they are directly communicating with each other.
Impact:
MitM attacks can lead to unauthorized access to sensitive information, financial theft, and data breaches. They are particularly dangerous because the victim may be unaware that their communication has been compromised.
Prevention:
Using encrypted communication channels (such as HTTPS), avoiding unsecured Wi-Fi networks, and implementing strong authentication methods can help prevent MitM attacks.
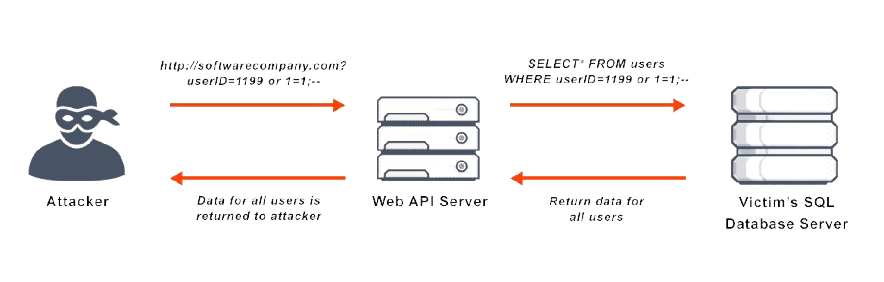
5. SQL Injection
SQL Injection is a type of cyberattack where attackers insert malicious SQL code into a web application’s input fields, exploiting vulnerabilities to access or manipulate the database.
How It Works:
Attackers target input fields like search boxes or login forms, injecting malicious SQL commands. If the web application fails to properly sanitize the input, the SQL code is executed, allowing attackers to view, modify, or delete data in the database.
Impact:
SQL Injection can lead to unauthorized access to sensitive data, data loss, or even complete control over the database. This type of attack can have severe consequences, especially if the compromised data includes customer information or financial records.
Prevention:
Proper input validation, using parameterized queries, and regularly updating and patching web applications can significantly reduce the risk of SQL Injection attacks.
6. Zero-Day Exploits
A Zero-Day Exploit occurs when attackers target vulnerabilities in software that are unknown to the vendor or developers. These vulnerabilities are exploited before a patch or fix is available, making them particularly dangerous.
How It Works:
Attackers identify and exploit unknown vulnerabilities in software, operating systems, or hardware. Since the vulnerability is not yet known to the vendor, there are no defenses or patches available to protect against the exploit.
Impact:
Zero-Day Exploits can lead to data breaches, unauthorized access, and system compromise. Because they exploit unknown vulnerabilities, they can bypass traditional security measures and cause widespread damage.
Prevention:
To mitigate the risk of Zero-Day Exploits, organizations should employ advanced security measures such as threat intelligence, behavior-based detection systems, and regular software updates.
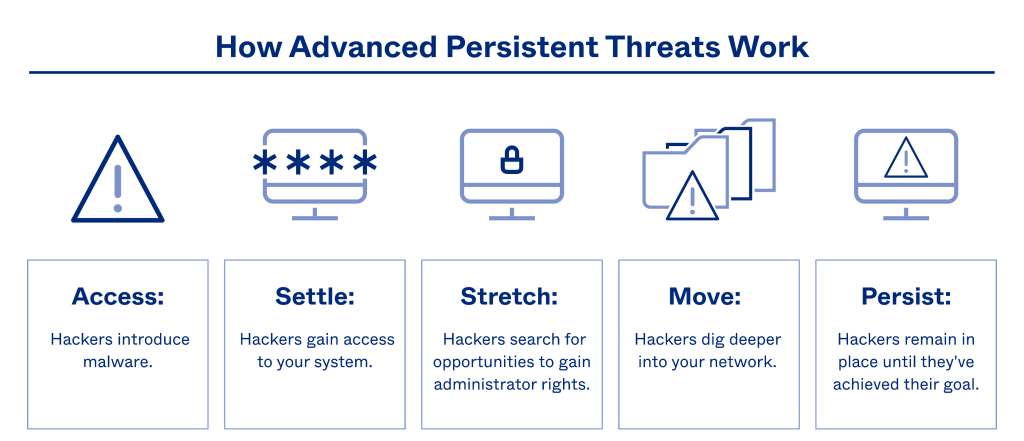
7. Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) are prolonged and targeted cyberattacks where attackers infiltrate a network and remain undetected for an extended period, often to steal sensitive data or spy on the organization.
How It Works:
APTs are typically carried out by well-funded and skilled attackers, such as nation-states or organized crime groups. They use a combination of tactics, including phishing, malware, and social engineering, to gain initial access and then move laterally across the network, maintaining a low profile to avoid detection.
Impact:
APTs can result in significant data breaches, intellectual property theft, and damage to national security or corporate secrets. The prolonged nature of these attacks means that attackers can gather substantial amounts of data over time.
Prevention:
Organizations should implement layered security defenses, including network segmentation, continuous monitoring, and threat intelligence to detect and respond to APTs. Employee training and strict access controls are also crucial in defending against these sophisticated threats.
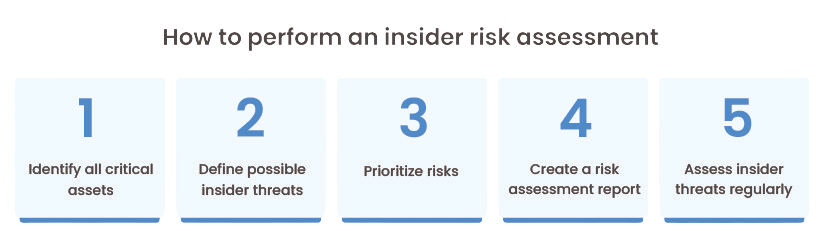
8. Insider Threats
Insider threats involve malicious activities carried out by individuals within the organization, such as employees, contractors, or business partners. These individuals have legitimate access to the organization’s systems and data but misuse that access for personal gain or to cause harm.
How It Works:
Insider threats can take many forms, including data theft, sabotage, or leaking confidential information. These attacks are particularly challenging to detect because the individuals involved have authorized access and often know how to avoid detection.
Impact:
Insider threats can lead to significant financial losses, data breaches, and reputational damage. Because insiders have direct access to critical systems, they can cause more damage than external attackers.
Prevention:
Preventing insider threats requires a combination of technical and organizational measures. Implementing strict access controls, monitoring user activity, conducting regular security audits, and fostering a positive workplace culture can help mitigate the risk of insider threats.
Lessons Learned and Why ConsultEdge.Global Can Help
These major cyberattacks serve as stark reminders of the ever-present threat landscape. Here are some key takeaways:
- Cybercriminals are constantly evolving their tactics, making it crucial to stay updated on the latest threats.
- Businesses of all sizes are potential targets, and no industry is immune.
- Implementing robust cybersecurity measures is essential for protecting data, systems, and critical infrastructure.
ConsultEdge.Global offers comprehensive cybersecurity solutions to help businesses of all sizes mitigate cyber risks.
Our services include:
- Vulnerability Assessments and Penetration Testing: Identify and address vulnerabilities in your IT infrastructure before they can be exploited.
- Security Awareness Training: Educate your employees on cybersecurity best practices to prevent social engineering attacks and phishing scams.
- Endpoint Security Solutions: Implement antivirus, anti-malware, and endpoint detection and response (EDR) solutions to protect your devices.
- Network Security Solutions: Firewalls, intrusion detection/prevention systems (IDS/IPS), and data loss prevention (DLP) solutions safeguard your network from unauthorized access and data breaches.
- Incident Response and Recovery Planning: Develop a plan to effectively respond to and recover from a cyberattack.
By partnering with ConsultEdge.Global, you can build a robust cybersecurity posture and protect your business from the ever-evolving threat landscape.
Empowering businesses to thrive in the digital age, ConsultEdge.Global is your trusted advisor for all your cybersecurity needs.

