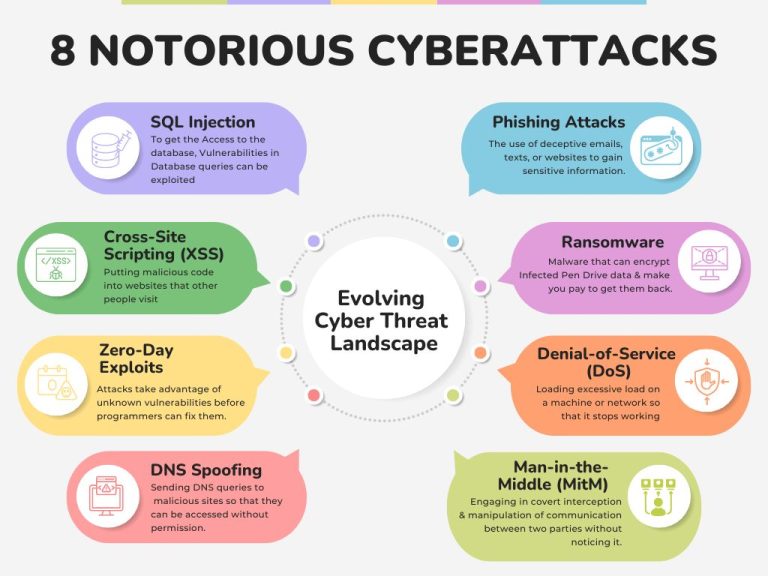
Technology & Innovation
CWPPs have emerged as a critical security layer for organizations leveraging the cloud. This article delves into the world of CWPPs, exploring their functionalities, market growth, and the factors...
CWPPs have emerged as a critical security layer for organizations leveraging the cloud. This article delves into the world of CWPPs, exploring their functionalities, market growth, and the factors...
Marketing & Sales
HR, Strategy & Operations
Unlock the secrets of MITRE ATT&CK + CTID: Learn how to anticipate & outmaneuver cyber attackers in 2023 & beyond...
As cloud adoption skyrockets, understanding cloud security is critical for IT auditors. This guide explores essential concepts, from shared...
Unlock Powerful Cloud Security Assessments: Elevate your organization's security posture with CloudFence.ai's free, comprehensive assessments...
Google, a trailblazer in the tech world, has just unveiled its latest marvel—Gemini. Deemed as the "most capable and general model" ever built by the...
Popular Posts

Risk Management & Cybersecurity
Cloud migration has become a strategic imperative for businesses of all sizes. The benefits are undeniable: increased scalability, agility, cost-efficiency, and access to cutting-edge technologies...
Harnessing the Power of AI with Microsoft Copilot: The Future of Productivity for Indian Businesses In an era where agility...
Microsoft Azure: Azure Cloud Services | Cloud Storage: Your Guide to Cloud Solutions In today’s digital landscape, businesses increasingly turn...
Strengthening Cyber Resilience: How to Address Today’s Cybersecurity Challenges In an era where technology drives every aspect of our lives...
CWPPs have emerged as a critical security layer for organizations leveraging the cloud. This article delves into the world of CWPPs, exploring their functionalities, market growth, and the factors...
Overview Of Client Business Model Industry – Business Consulting Firm Location – Gurugram, Haryana This Organization is one of the...
Introduction In June 2011, a former Citigroup executive allegedly stole more than $19 million from Citi and its customers1. In...
How is USB encryption helping secure data transfer? As the workforce becomes mobile, the necessity of USB media is undeniable...